LDAP Integration Guide
Usage scenarios
LDAP (Lightweight Directory Access Protocol) login is an authentication method based on directory services. After it is turned on, users can log in to the HAP platform using their domain account and password.
Prerequisites
- The HAP server can access the domain server
- Account password that can log in to the domain
Steps
Fill in parameters
-
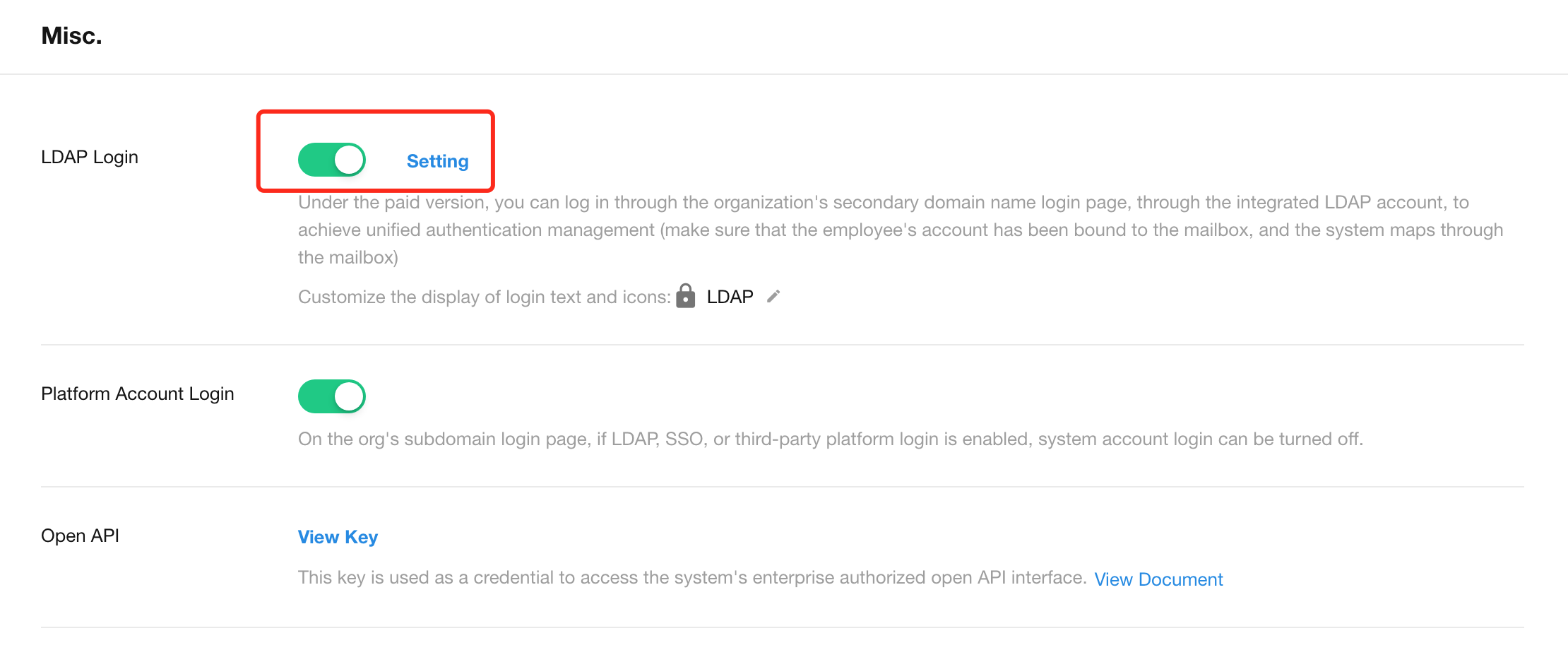
In the HAP system, enter Org Admin > Misc. and enable LDAP Login, as shown in the figure below��:
-
Configuration parameters-Server settings
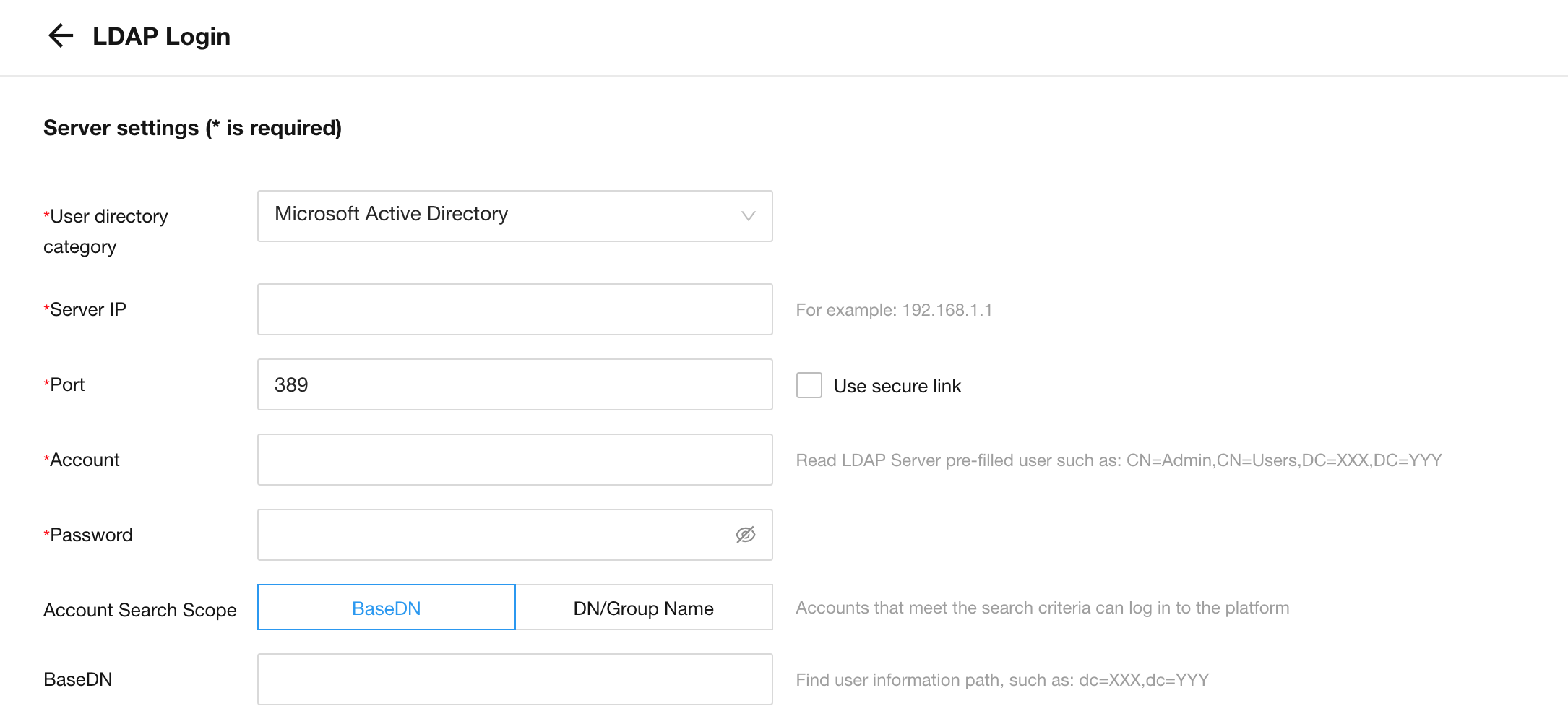
- User directory category;For Microsoft AD, just select
Microsoft Active Directory. The libraries used by other types are slightly different, but the functions are roughly the same - Server IP;Domain server IP, such as
192.168.1.1 - Port; Default
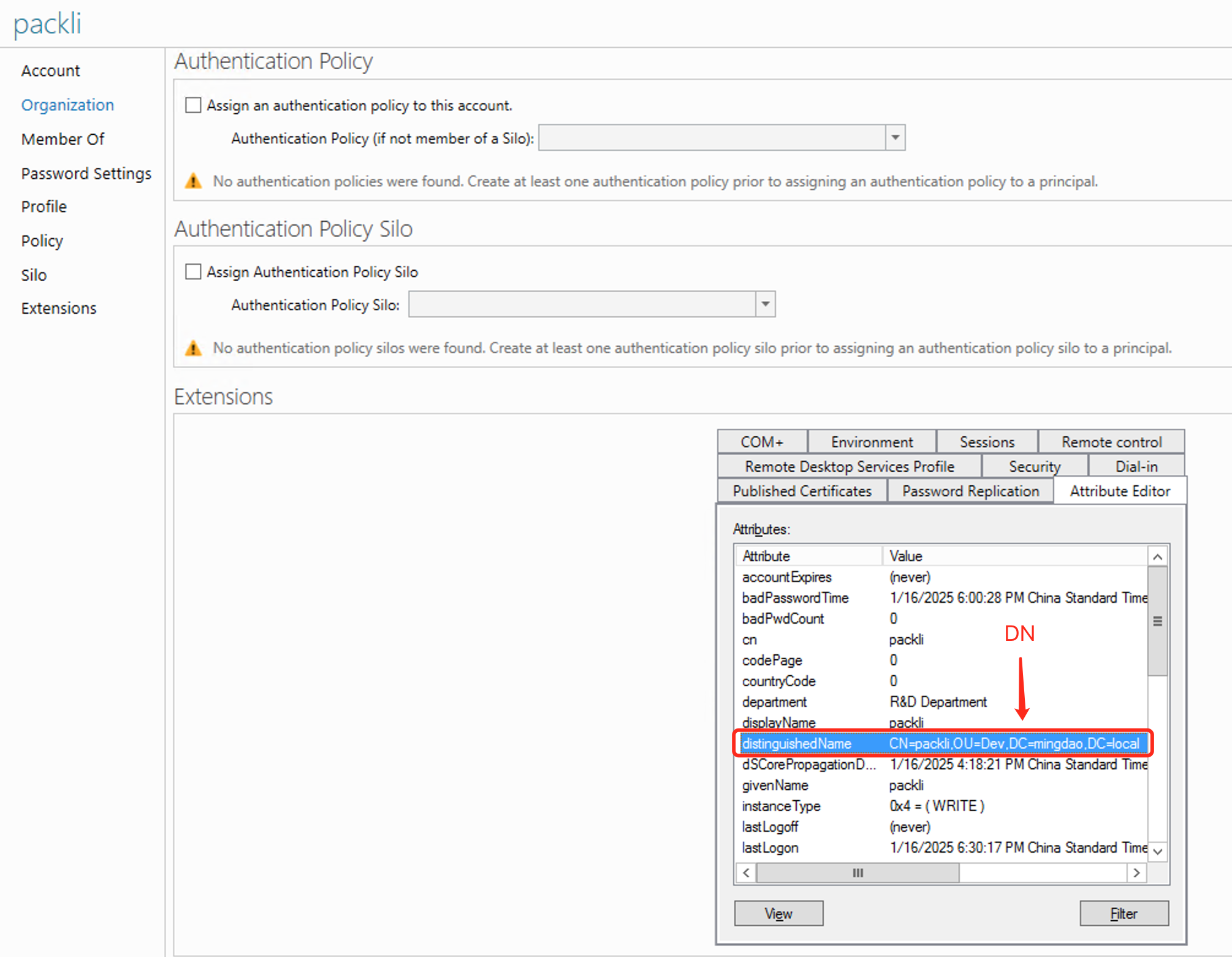
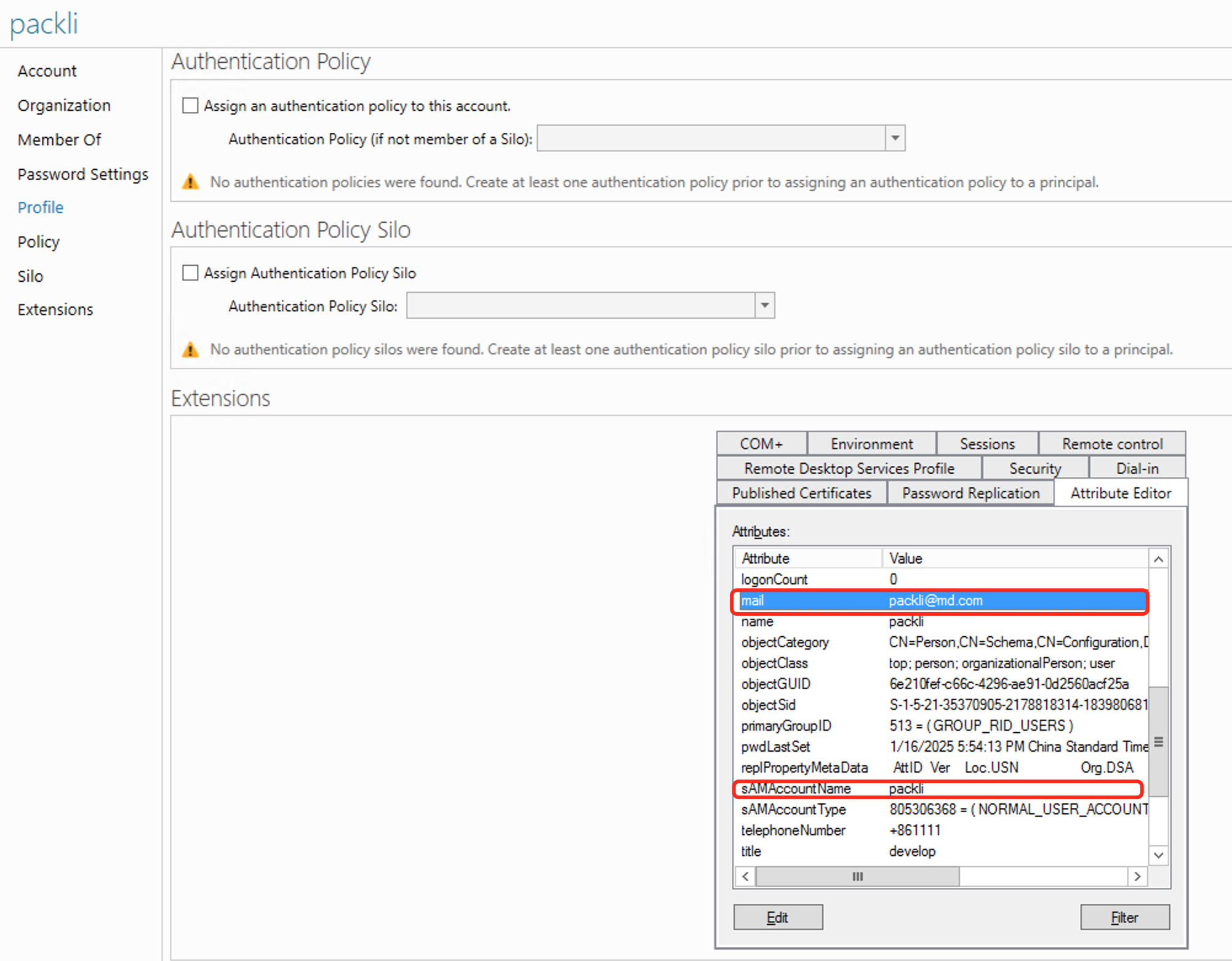
389, use secure connection by default636, the spliced address isldap://192.168.1.1:389orldaps://192.168.1.1:636 - Account; Fill in the DN(distinguishedName) attribute value of the domain user, such as
CN=packli,OU=Dev,CN=Users,DC=hap,DC=local, not allowed Fill in the user name, such aspackli,admin,user1 - Password; Password in the domain
- Account Search Scope; you can choose to search by DN scope or search by DN group
- BaseDN; fill in the DN attribute value, such as
CN=Users,DC=hap,DC=local, which means the search scope is users under the current DN. Users who are not under the current DN cannot log in. If not filled in, the default is Root DN such asDC=hap,DC=local - DN/Group Name; multiple DN groups can be configured. The first input box is filled with the group DN value, and the second input box is filled with the group alias; for example, the group DN value is
CN=dev-Group1,OU= Dev,DC=hap,DC=local, the group name isldap development group; this function requires the DN type to be a group, and detects whether the logged-in domain user is a member of one of the groups. If he is not a member, he cannot log in.
- BaseDN; fill in the DN attribute value, such as
- User directory category;For Microsoft AD, just select
-
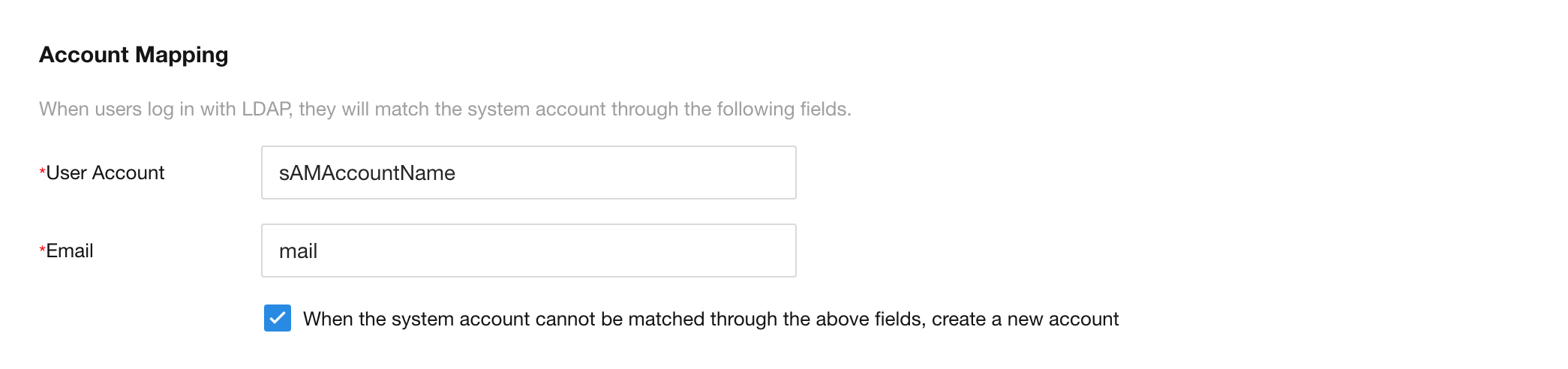
Configuration parameters-Account Mapping
-
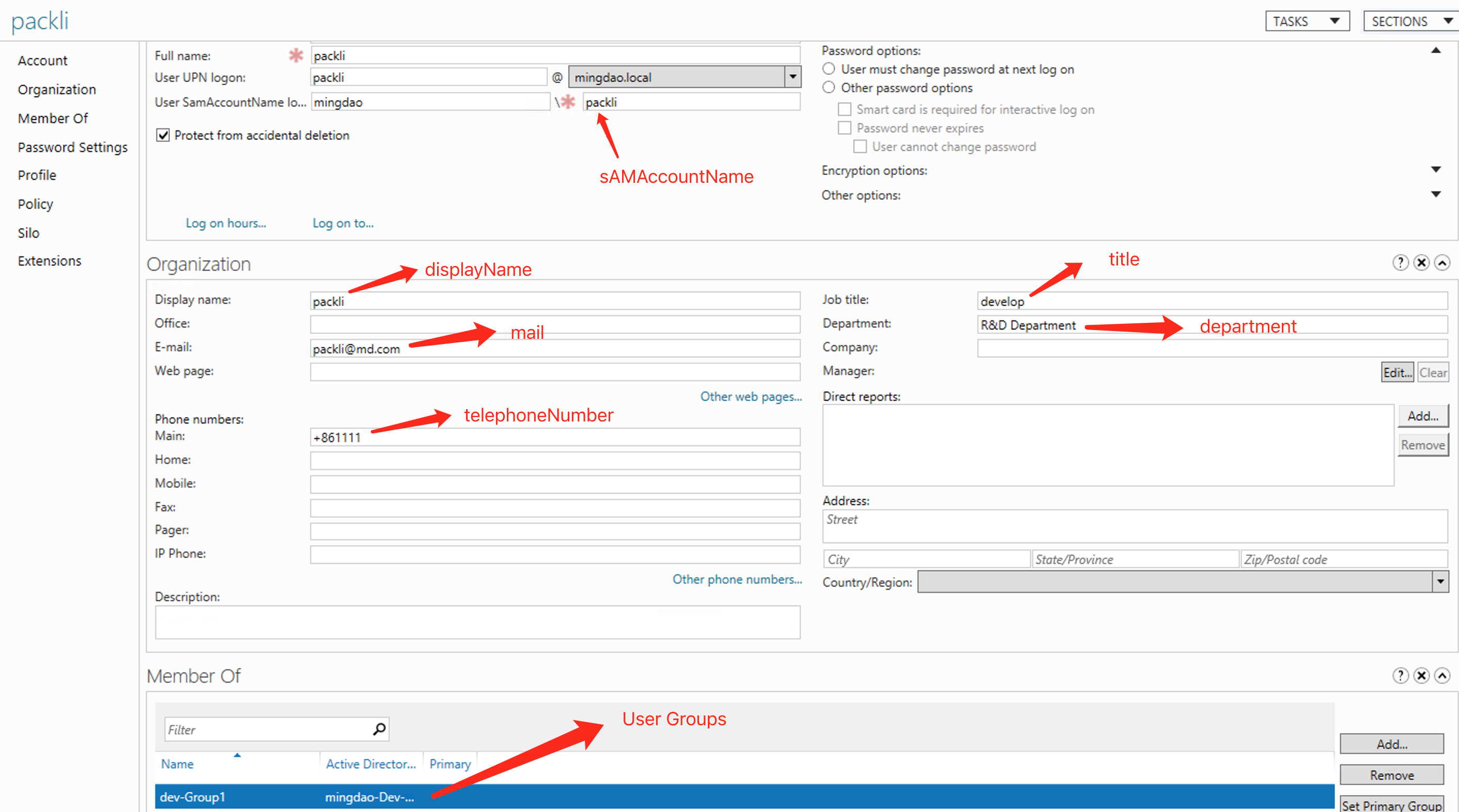
User Account; fill in the domain user User SamAccountName logon to match the login account, the default is
sAMAccountName; if the value of user sAMAccountName is peter, then the user name for LDAP login is also peter -
Email; fill in the domain user's email, the default is
mail; used to create or find users -
CheckBox; When the system account cannot be matched through the above fields, create a new account
- YES; If the domain account does not have any binding relationship, or the domain mailbox does not exist in the HAP system, a new HAP account will be created
- NO; If the domain account has a binding relationship, it is regarded as the same user; or if the domain mailbox exists in the HAP system, it is regarded as the same user; if the domain account has a binding relationship (interface synchronization or single point binding), the domain mailbox will be automatically overwritten HAP account email address
-
-
Configuration parameters-Sync Information
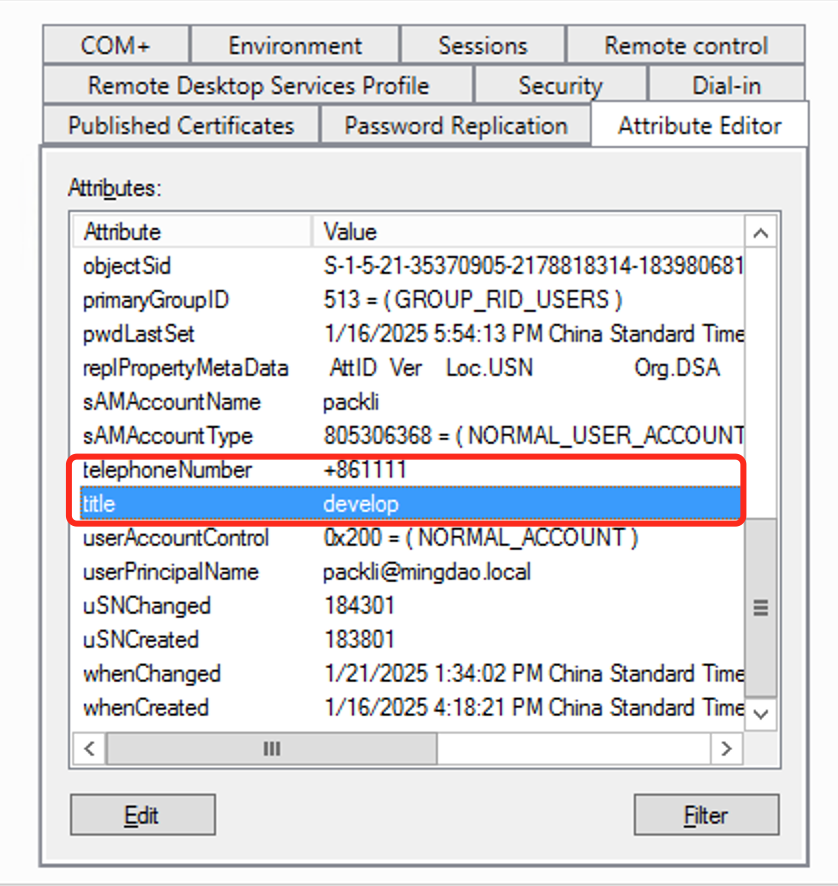
-
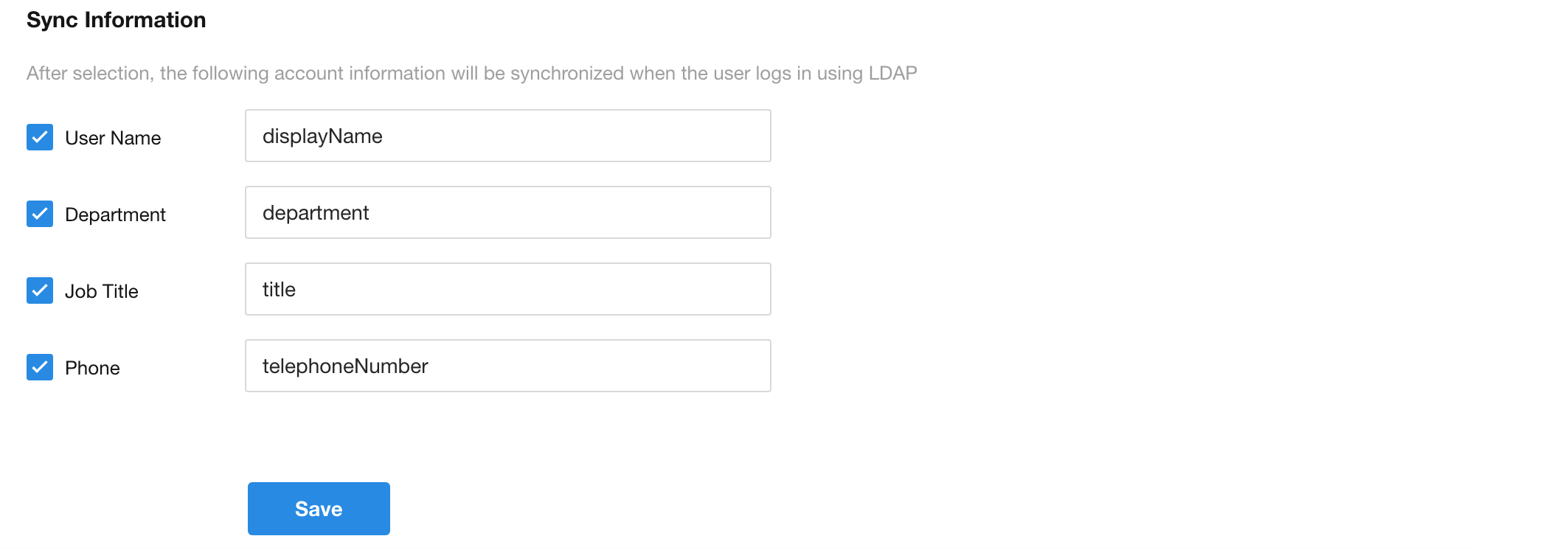
User Name; mapping domain user name, default
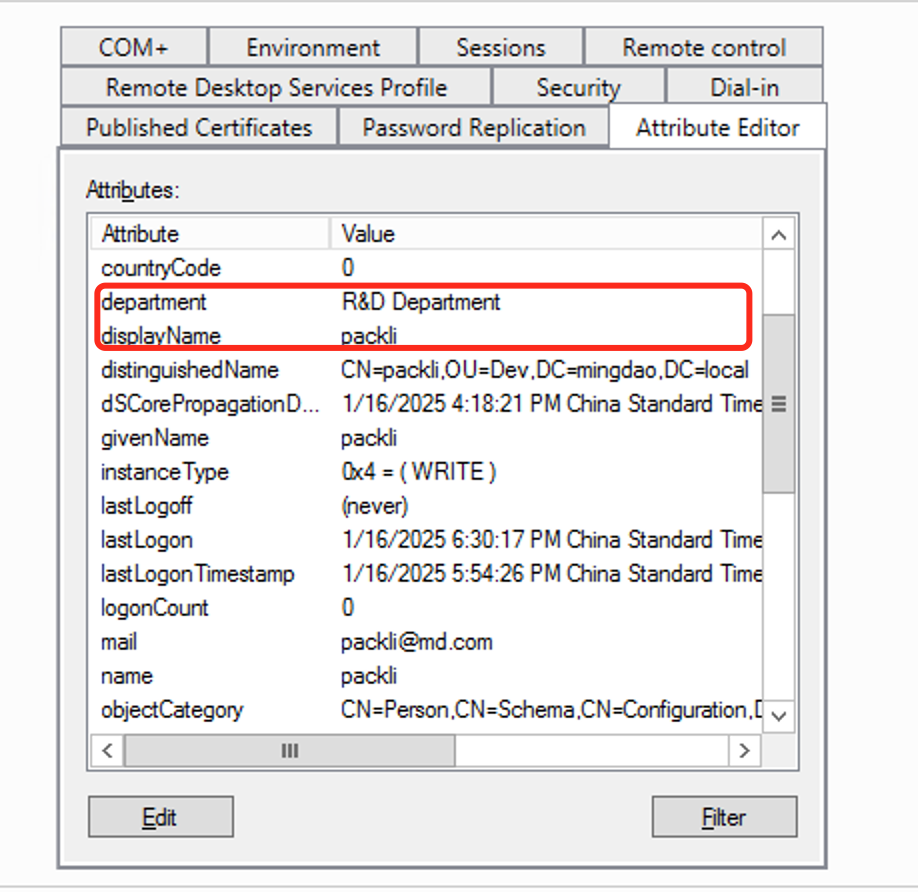
displayName; corresponding to HAP Personnel Info-Name -
Department; mapping domain user Department, default
department; corresponding to HAP Personnel Info-Department -
Job Title; maps domain user Job title, default
title; corresponds to HAP Personnel Info-Job Title -
Phone; Maps the Phone numbers-Main of the domain user, defaults to
telephoneNumber; corresponds to the HAP Personnel Info-Work Phone (not a personal mobile phone number)
-
-
Save
The saving operation will verify whether the server IP of Server settings is smooth and whether the account password is correct.
-
If there is no response for a long time after saving, the IP connection may be blocked.
-
If it prompts that the connection failed immediately after saving, it may be that the account and password verification failed.
-
The user account filled in is not the domain DN attribute and may fail to be saved.
-
Test login
-
Enter the LDAP user account
sAMAccountNamevalue or other unique attribute value configured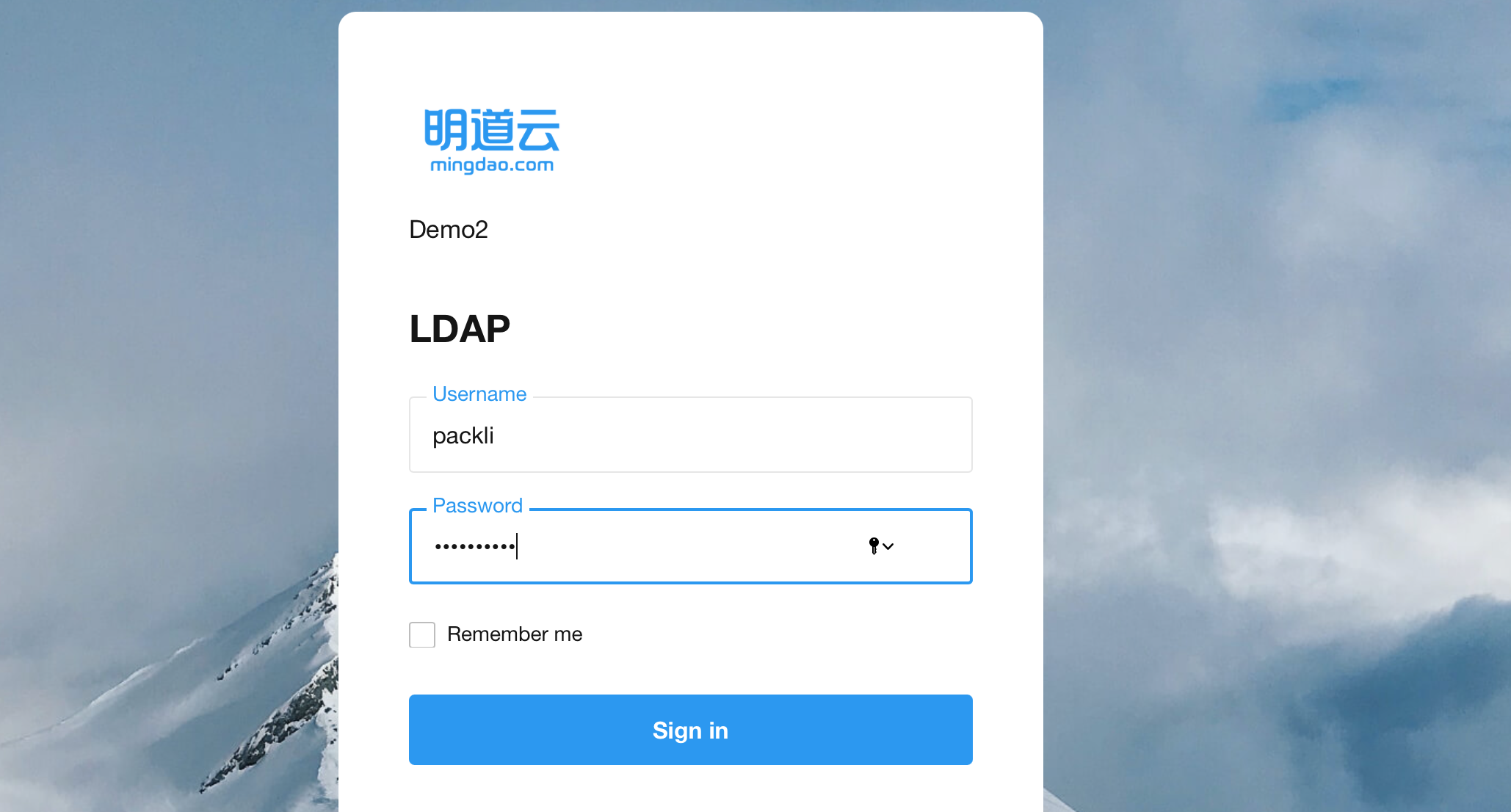
-
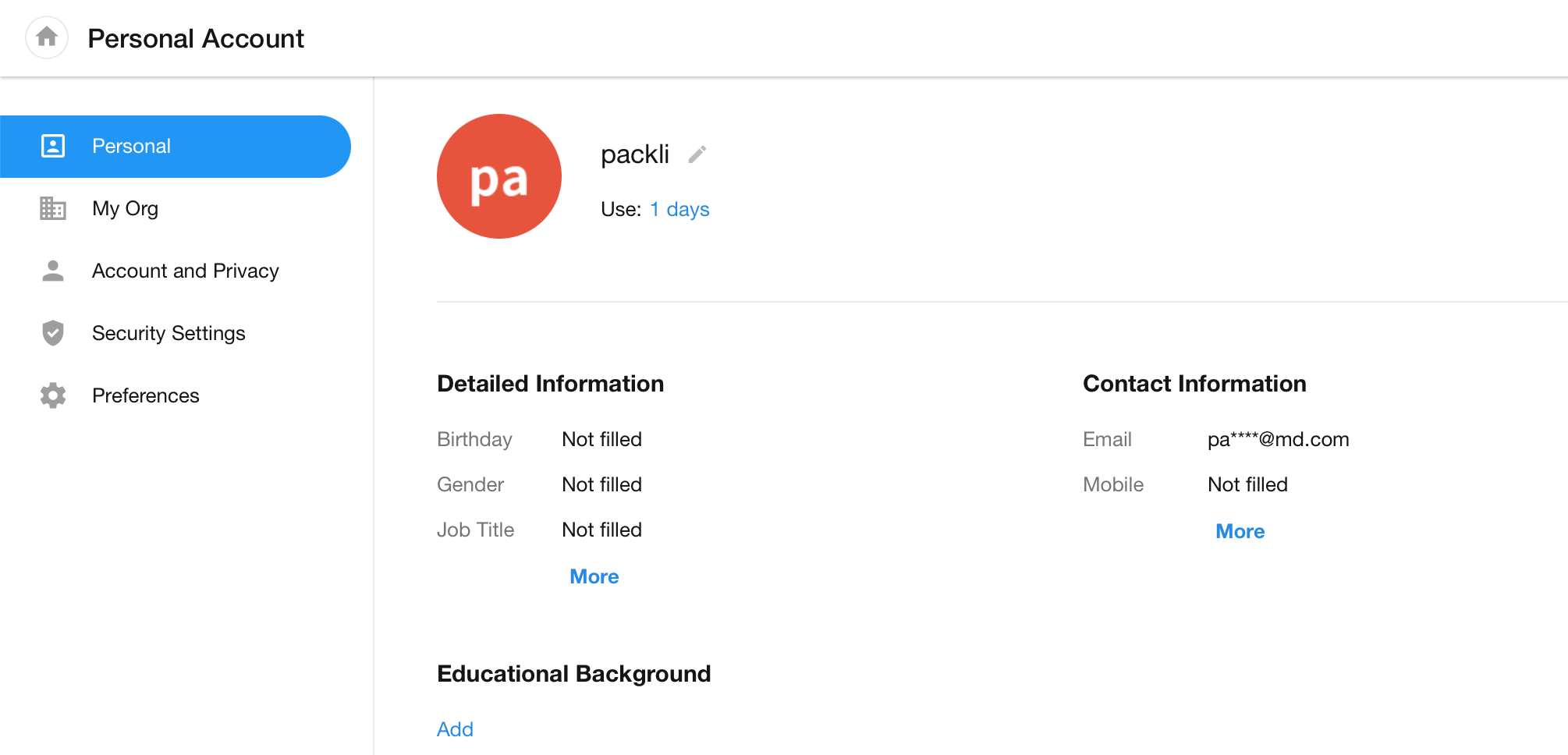
After successful login, check whether the account is mapped correctly
-
Troubleshooting login failures, generally only prompts that the username or password is incorrect
-
Private Deployment Platform administrator logs in to HAP, click on the avatar in the upper right corner: Platform Mgt > Ops Mgt >Log; retrieve the log with Service Name as
sso, and check the specific cause of the error. -
SAAS You need to contact the platform administrator to view the log
-
Common errors in sso logs
- Incorrect account password
-
The account does not exist, it is visible in the sso log,
No users found -
Password error, visible in sso log,
error authenticate ERROR: xxx: {"lde_message":"80090308: LdapErr: DSID-0C090446, comment: AcceptSecurityContext error, data 52e, v2580\u0000","lde_dn":null}
- Search scope error
-
No users found in the DN scope, visible in the sso log,
No users found -
There is a problem with the DN of the user or group not found under the DN group, which can be seen in the sso log,
checkIsUserMemberOf ERROR: dn group illegal, find Group xxx: false
- Failed to save LDAP configuration
- The account used in the configuration is not a domain DN attribute, which is visible in the sso log.
LDAPError [InvalidCredentialsError]: 80090308: LdapErr: DSID-0C090446, comment: AcceptSecurityContext error, data 52e, v2580